Section 7.2 Data Encryption Standard
Objectives
- Lucifer
- Really SImple DES
- DES
Subsection 7.2.1 A Little History
Subsection 7.2.2 Overview Really Simple DES
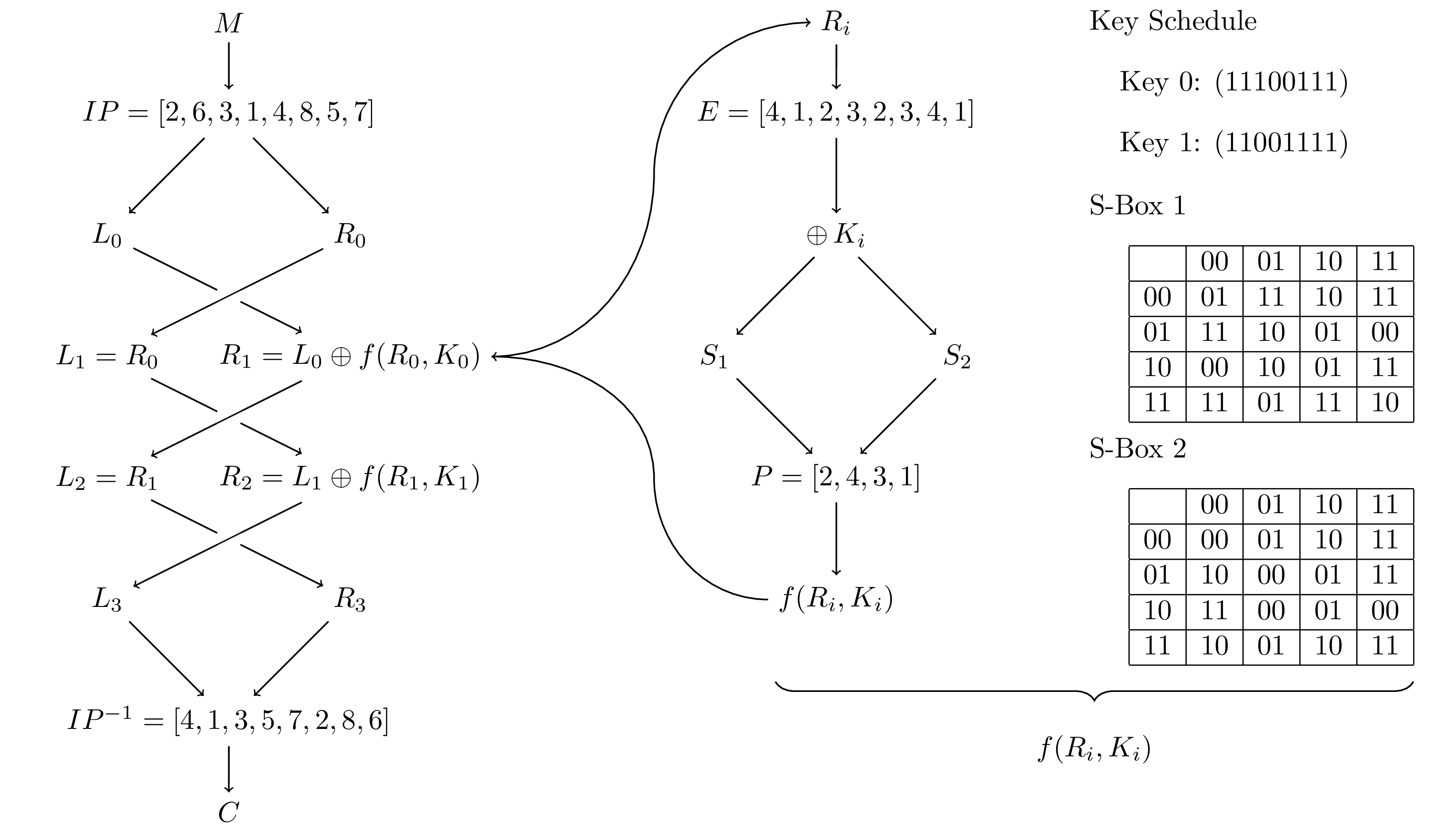
The algorithm for the really simple data encryption standard follows this general pattern:
- Create a Key Schedule, assume the keys are each 8 bits; a group of 8 bits is called a byte
- Convert the input into a stream of bits
- Split the bit stream into bytes
- Permute the entries in each byte
- Run the permuted byte through two enciphering rounds with the function\(f(R_i,K_i)\)
- Swap the left and right in the final round
- Apply the inverse of the initial permutation
The diagram below gives a little more detail and we will walk through this a bit at a time in this section.
Example 7.2.2. Encipher “bye”: Key Schedule.
Starting with the initial 32 bit key:
we generate a key schedule in which key 0 consists of bits 1 through 8, key 1 is bits 2 through 9, key 3 is bits 3 through 10, etc.. Doing this the first five keys are:
Checkpoint 7.2.3. Expanding a Key Schedule.
Continuing with the main key:
find keys \(Key\ 6\text{,}\) \(Key\ 7\text{,}\) and \(Key\ 8\text{.}\)
Checkpoint 7.2.4. Finding Another Key Schedule.
Using the key:
find keys \(Key\ 0\text{,}\) \(Key\ 1\text{,}\) \(Key\ 2\text{,}\) and \(Key\ 3\text{.}\)
Example 7.2.5. Encipher “bye”: Convert and Split.
Suppose we want to encipher “bye” using the Table 7.1.14 we get:
which we expand to
the the number of bits is a multiple of 8. Now spliting this into bytes we get three pieces:
Next we will need to look at how we permute the bits in each sub piece in order to start enciphering.
Checkpoint 7.2.6. Encipher “hi”: Convert and Split.
Suppose we want to encipher “hi”. Use Table 7.1.14 to convert this to bits, and then split it up into bytes.
Be sure to look back at Subsection 7.1.2 to review looking up characters in the ASCII table. Also, remember to tack on a couple of extra 0 bits at the start in order to make the length of the message a multiple of 8.
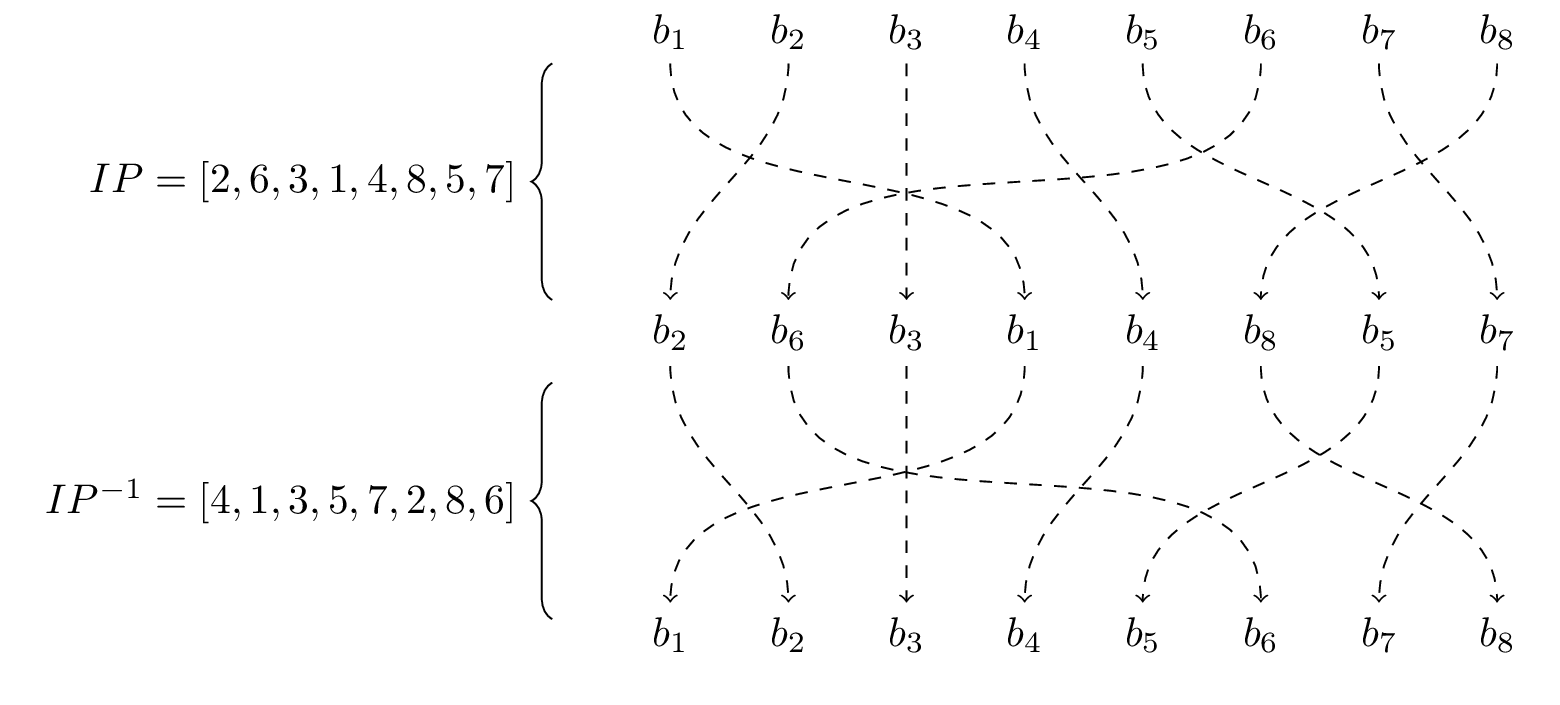
Subsection 7.2.3 Permutation
As part of the encryption process each byte of information will be run through a fixed initial permutation before enciphering and through the inverse of the permutation at the end. The permutation we will be using is:
Once we have completed all the rounds of the Feistel cipher that is at the heart of DES we will apply the inverse permutation:
As we can see in Figure 7.2.7 if there were no intermediate steps this would just give us back the exact same byte.
Example 7.2.8. Encipher “bye”: Initial Permutation.
If we take the first byte in our example above
and permute it we get
We can then split this into left and right nibbles (a set of 4 bits, and in case you were wondering 2 bits is a crumb) in preparation for enciphering:
Checkpoint 7.2.9. Encipher “hi”: Initial Permutation.
If you started with \(M_1=(00110100)\) what would you get by applying \(IP\) and then splitting the message into \(L_0\) and \(R_0\text{?}\)
\(L_0=0110\) and \(R_0=1000\)
Subsection 7.2.4 Enciphering Function
Now that we have an initial pair of left and right nibbles we are ready to start the process of shuffling them together with our Feistel cipher. As usual
and
But unlike the simple \(f\) in Section 7.1, here the function combining \(R_0\) and \(K_0\) is devilishly complicated; this is what gives DES its strength.
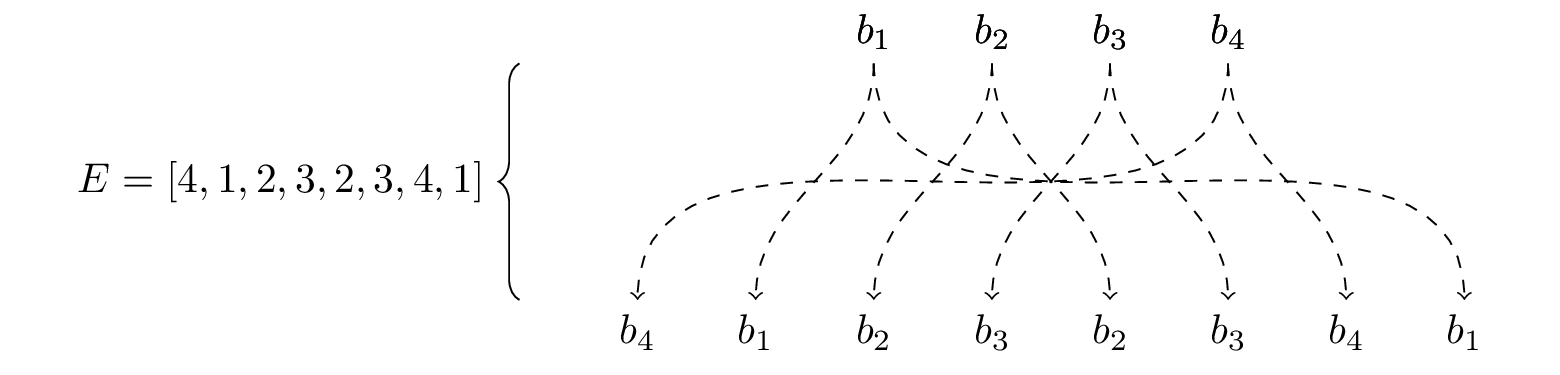
- Expand the right half to 8 bits
- Add the round key
- Use the S-boxes to reduce the 8-bits back to 4
- Permute the 4 bits
The first couple of steps and the last step are fairly straight forward and we will look at them just below. They work in ways similar to the permutation above and to the Feistel cipher we had discussed before. The third step will need more discussion.
The first step in the round function is to expand the 4-bit nibble \(R_i\) into an 8-bit byte so that it can be added to the round key \(K_i\text{.}\) This is expressed in the diagram as
which we read in much the same way we read the initial permutation \(IP\text{.}\)
Once this is done we can add the expanded right side and the key as we have before:
Example 7.2.11. Encipher “bye”: Expansion and Key.
The initial left and right nibbles are
The next left side is \(L_1=R_0=(1 0 1 0)\text{.}\) To find the next right side we first run \(R_0\) and \(K_0\) through the round function which begins by expanding and adding the key.
The result of this needs to be run through the s-boxes to compress this output back to a nibble.
Checkpoint 7.2.12. Encipher “hi”: Expansion and Key.
What do we get if we expand \(R_0=1000\) and add it to the key \(k_0=11100100\)
The s-boxes serve the opposite roll of the expansion; they turn bytes into nibbles. To compress the byte,
- split it into two nibbles,
- run the first nibble through s-box 1,
- run the second nibble through s-box 2, and
- put the output crumbs back together into a single nibble.
We send a nibble through an s-box by using the first two bits as the row label and the second as a column label, where they intersect is the output. For example in s-box 1 below the nibble (1101) leads us to row (11) and column (01) so that the output is (01).
| 00 | 01 | 10 | 11 | |
| 00 | 01 | 11 | 10 | 11 |
| 01 | 11 | 10 | 01 | 00 |
| 10 | 00 | 10 | 01 | 11 |
| 11 | 11 | 01 | 11 | 10 |
| 00 | 01 | 10 | 11 | |
| 00 | 00 | 01 | 10 | 11 |
| 01 | 10 | 00 | 01 | 11 |
| 10 | 11 | 00 | 01 | 00 |
| 11 | 10 | 01 | 10 | 11 |
Example 7.2.15. Encipher “bye”: Finishing the Round.
After expanding and adding the key we are left with the byte \((10 11 00 10)\) which gives two nibbles:
Running \(n_1\) through s-box 1 we get (11) and \(n_2\) through s-box 2 gives (10). These combine to give the nibble (1110).
The last step is to apply the permutation \(P=[2,4,3,1]\) to get:
Adding this to \(L_0=(0000)\) we finally get
Checkpoint 7.2.16. Encipher “hi”: Finishing the Round.
Use the s-boxes to compress \((10100101)\) down to a nibble and apply the final permutation \(P\text{.}\)
\(f(R_0,k_0)=1000\)
Subsection 7.2.5 Finishing Enciphering
Looking at Figure 7.2.1 we see that we run the left and right pieces through the cipher function two times total, swap the sides so that deciphering will work identically to enciphering, and finally apply the inverse of the initial permutation.
Example 7.2.17. Encipher “bye”: Completing Encryption.
Starting with \(M_1=(0 0 0 1 1 0 0 0)\) we now have:
Running through second full round gives us \(L_2=(1011)\) and
Swapping sides without using the function gives
Finally putting these together, (0101 1011), and applying \(IP^{-1}\) we get
Checkpoint 7.2.18. Encipher “hi”: Completing Encryption.
Given \(L_1=1000\) and \(R_1=1110\) use the key \(k_1=11001001\) to go through another round with the enciphering function, and then finish the enciphering process.
Subsection 7.2.6 A Little More Practice
Checkpoint 7.2.19. Encipher \(M_2\).
(a)
Apply the initial permutation IP to \(M_2=(10111100)\) and split it into \(L_0\) and \(R_0\text{.}\)
\(L_0=0111\) and \(R_0=1010\)
(b)
Expand \(R_0\) with \(E=[4,1,2,3,2,3,4,1]\) and add round key \(Key\ 2=10011110\text{.}\)
\(E(R_0)\oplus K_2 = 1100\, 1011\)
(c)
Apply the s-boxes to \(E(R_0)\oplus K_2 = 1100\, 1011\) to reduce it to a nibble, and then apply the permutation \(P=[2,4,3,1]\text{.}\)
\(f\left(R_0,K_2\right)=1001\)
(d)
Add \(f\left(R_0,K_2\right)=1001\) to \(L_0\) in order to get \(R_1\text{.}\)
\(L_1=1010\) and \(R_1=1110\)
(e)
Run \(L_1=1010\) and \(R_1=1110\) through another full round using the \(Key\ 3=00111100\) in order to get \(L_2\) and \(R_2\text{.}\)
\(L_2=1110\) and \(R_2=0111\)
(f)
Swap the left and right sides one more time, without applying the function, and then apply \(IP^{-1}\) to get \(C_2\text{.}\)
\(C_2=10111101\)
Checkpoint 7.2.20. Encipher \(M_3\).
(a)
Apply the initial permutation IP to \(M_3=(11100101)\) and split it into \(L_0\) and \(R_0\text{.}\)
\(L_0=1111\) and \(R_0=0100\)
(b)
Expand \(R_0\) with \(E=[4,1,2,3,2,3,4,1]\) and add round key \(Key\ 4=01111001\text{.}\)
\(E(R_0)\oplus K_4 = 0101\, 0001\)
(c)
Apply the s-boxes to \(E(R_0)\oplus K_4 = 1100\, 1011\) to reduce it to a nibble, and then apply the permutation \(P=[2,4,3,1]\text{.}\)
\(f\left(R_0,K_4\right)=0101\)
(d)
Add \(f\left(R_0,K_4\right)=0101\) to \(L_0\) in order to get \(R_1\text{.}\)
\(L_1=0100\) and \(R_1=1010\)
(e)
Run \(L_1=0100\) and \(R_1=1010\) through another full round using the \(Key\ 5=11110010\) in order to get \(L_2\) and \(R_2\text{.}\)
\(L_2=1010\) and \(R_2=1010\)
(f)
Swap the left and right sides one more time, without applying the function, and then apply \(IP^{-1}\) to get \(C_3\text{.}\)
\(C_3=01111000\)
Checkpoint 7.2.21. Encipher \(M_4\).
Suppose that there is a fourth part to our message \(M_4=01110011\text{.}\)
(a)
Apply \(IP\) to \(M_4\) and split it to get \(L_0\) and \(R_0\text{.}\)
\(L_0=1010\) and \(R_0=1101\)
(b)
Now find the next set of nibbles \(L_1\) and \(R_1\text{,}\) use the round key \(Key\ 6=11100101\text{.}\)
\(L_1=1101\) and \(R_1=0000\)
(c)
Now find the next set of nibbles \(L_2\) and \(R_2\text{,}\) use the round key \(Key\ 7=11001010\text{.}\)
\(L_2=0000\) and \(R_2=0000\)
(d)
Now find the next set of nibbles \(L_3\) and \(R_3\text{.}\)
\(L_3=0000\) and \(R_3=0000\)
(e)
Finish up the enciphering process.
\(C_4=0000 0000\)
Checkpoint 7.2.22. Sample Decipherment.
Decipher the message \(C=10000100\) which was enciphered using the two keys \(k_2=10010010\) and \(k_3=00100100\text{.}\)