“Say for example we mutually establish k as the index of the mobile circle. Writing, the formulae are positioned at will, say such k lies under the uppercase B [Figure 3.1.2] and the next letter corresponds to the letter that comes next. In writing to you, I will first put the uppercase B under which lies the index k in the formula; this is to signal you far away, wanting to read what I have written, that you should set up the twin formula in your keeping, positioning the mobile circle so that the B sits over the index k. Then all of the rest of the lowercase letters present in the coded text will take their meaning and sound from those of the fixed circle above them.”
“After I have written three or four words I will mutate the position of the index in our formula, rotating the disk let's say, so that the index k falls below the upper case R. Then in this missive I write an uppercase R to indicate that k no longer refers to B, but to R, and the letters that will follow will assume new meanings.” - Alberti [17, p. 181]
Section D.3 Chapter 3 Quotes:
Alberti's Polyalphabetic Cipher:
Vigenère's Polyalphabetic Cipher:
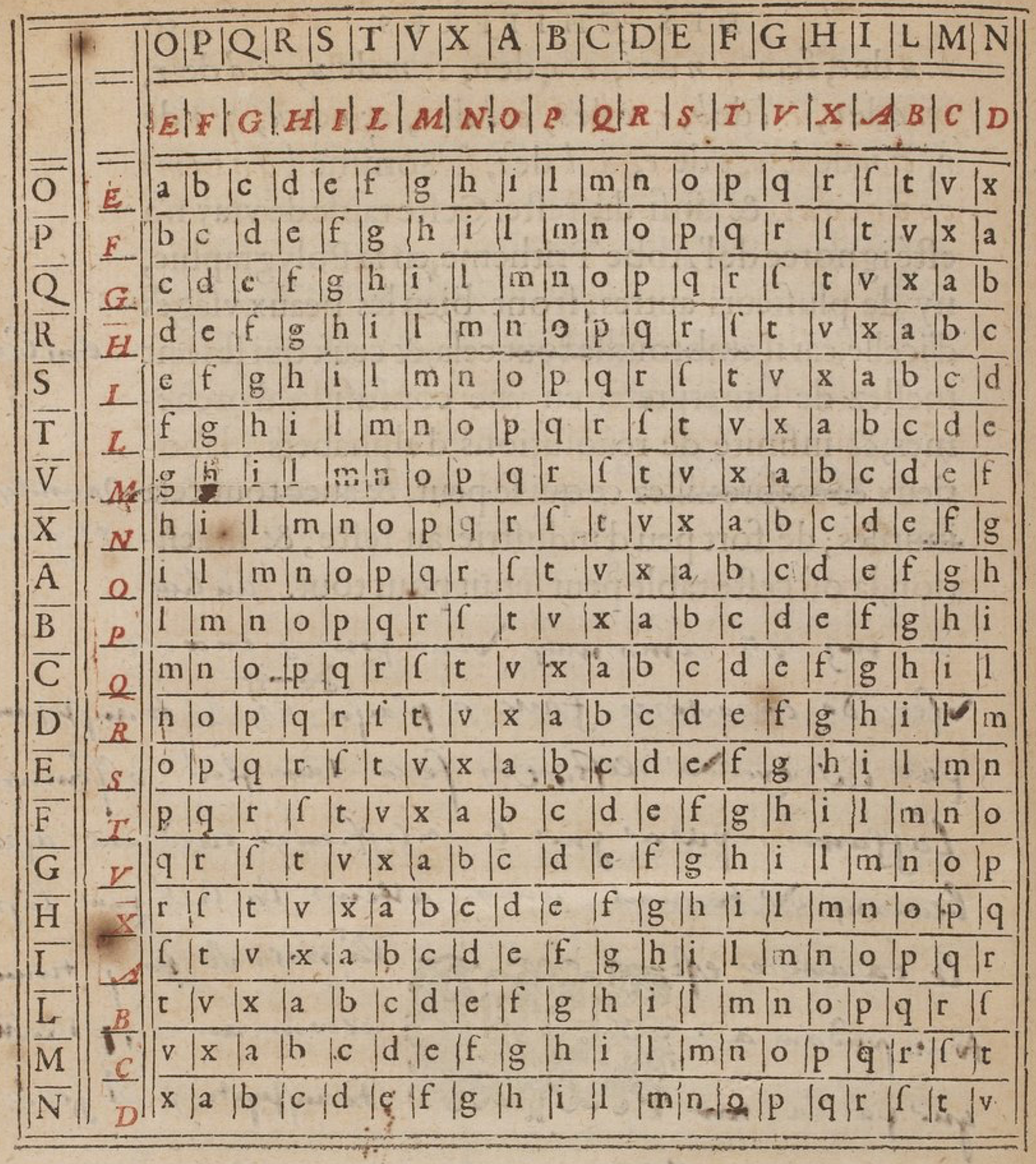
“... set the capitals which run across the top [of the table] for the message to be conveyed & those that run perpendicularly down the left for the keys. I have put two rows of capitals here, one black and the other red, to show that alphabets of the text as, the keys, may be transposed and changed in as many ways as you want to keep knowledge of them from all others except ones correspondents. Therefore, to encipher the saying we used previously “au nom de l'eternel,” with the key “le jour obscur” proceed in this way; from a in the alphabet across the top in red, come to the row with l and the box with b: u from e will be q: n from i, n: o from o, s: m from u, a: d from r, m: e from o, i: l from b, c: e from s, o: t from c, n: e from u, q: r from r, c: n from l, o: e from e, a: l from i, l. Altogether we get bqnsamiconcoal & so on for the remainder.” [16, pp. 49b, 50, 50b (100-102)], [11, p. 110] 1 Most of this translation is due to Mendelsohn [11], I have only filled in with my own at the end which he had not translated.
Agripa's Pigpen Cipher
One may frame nine chambers by the intersection of four parallel lines intersectiong themselves at right angles as expressed in the figure:
Which being dissected into parts generates nine the particular figures:
from the nine chambers. Characterize each letter in a chamber by the notation of one point to show the first letter in the chamber; two for the second letter; three for the third letter; so that the characters of Michael may be written in seven characters:
Which may be written one after another drawn as three figures:
Which written one after another drawn as one figure, omitting the usual marks, gives the characters of Michael as:
[1, Vol. 3, CCLXXV (p.279)] [2, Vol.3, Chapter XXX] 2 The translation is based, for the most part, on [2] with reference to the original text. The example was changed some in order to make the work more accessible.`
Vigenère's Autokey Cipher
“Each letter may be enciphered by the preceding letter, thus: with the . . . text. . . . “Au nom de l'eternel” and the key D, we say, a [the first letter of the text] from D [the key letter] gives x; u [the second letter of the text] from A [the first letter of the text, which now becomes the key] gives i; n from U, a; o from N, h; m from O, g; d from M, u; e from D, p; l from E, t; e from L; m, t from E, l; e from T, s; r from E, h; n from R, i; e from N, x; l from E, t. By which method, taking D for the key, we would arrive at DXIAHGUPTMLSHIXT. The other method, which is more secret, is to encipher each letter of the clear text not by the letter [of that text] which precedes it, but by the letter by which the preceding letter is enciphered. Thus, a from D, which is the key, gives x; u from X [the first letter of the cipher text] h; n from H, e; o from E, e; m from E, c; d from C, o; e from O, u; l from U, m; ... etc.” [16, pp. 49-49b] [11, p. 128]
